It appears that France's Assemblee Nationale recently voted on legislation requiring all entities that provide cryptographic services to turn over the keys to law enforcement. According to Ammendment CL262 of Article 6 here...http://www.assemblee-nationale.fr/14/amendements/2669/CION_LOIS/CL262.asp "persons or entities who provide cryptology services are now compelled to promptly return to the agents of intelligence services decryption keys". Privacy advocates are going to try and have a field day with this one.
↧
Cryptographic Service Providers in France Have To Abide By A New Law
↧
Internet Society Network and Distributed System Security Symposium (NDSS) 2015 Programme Papers
Papers can be accessed here http://www.internetsociety.org/events/ndss-symposium-2015/ndss-2015-programme which cover topics such as Web Security, Mobile Security, Detection/Analysis/Prevention/Response, Privacy, Social Networks & Cloud Services and Authentication. Some titles names are "Identifying Cross-origin Resource Status Using Application Cache", "Parking Sensors: Analyzing and Detecting Parked Domains", "Upgrading HTTPS in mid-air: An empirical study of strict transport security and key pinning", "Information Flow Analysis of Android Applications in DroidSafe", "What's in Your Dongle and Bank Account? Mandatory and Discretionary Protection of Android External Resources" and much more.
↧
↧
Truecrypt audit report released
A few weeks back I wrote an update on the Truecrypt audit promising that we'd have some concrete results to show you soon. Thanks to some hard work by the NCC Crypto Services group, soon is now
more here.........http://blog.cryptographyengineering.com/2015/04/truecrypt-report.html
more here.........http://blog.cryptographyengineering.com/2015/04/truecrypt-report.html
↧
Snippet Detector
One year ago I blogged about a tool of mine I use to recognize snippets from a disassembled binary file. The tool often speeds up my dead list analysis process. The annoying thing is that it works in cooperation with IDA, and it’s somehow a waste of time because I have to switch from one program to another and vice versa a lot of time. Since of IDA is the most used disassembler program out there I decided to morph my project into an IDA Python scripts project.
The project is called Snippet Detector (SD in short), and the aim is to collect as many disassembled snippets as I can. At the moment a snippet is indeed a defined function and it’s everything saved inside a database. The info inside the database can be later applied to a new disassembled file hoping to find one or more matches.
more here..........https://zairon.wordpress.com/2015/03/31/snippet-detector/
The project is called Snippet Detector (SD in short), and the aim is to collect as many disassembled snippets as I can. At the moment a snippet is indeed a defined function and it’s everything saved inside a database. The info inside the database can be later applied to a new disassembled file hoping to find one or more matches.
more here..........https://zairon.wordpress.com/2015/03/31/snippet-detector/
↧
Exploiting PHP Bug #66550 - SQLite prepared statement use-after-free - [A local PHP exploit]
As the title says, this bug is useful only for post exploitation to bypass protections when the attacker already has arbitrary PHP code execution. Nevertheless, this was a good exploit exercise.
more here.......http://v0ids3curity.blogspot.de/2015/04/exploiting-php-bug-66550-sqlite.html
more here.......http://v0ids3curity.blogspot.de/2015/04/exploiting-php-bug-66550-sqlite.html
↧
↧
Using the docker command to root the host (totally not a security issue)
Docker is an awesome tool that allows their users to create, manage and run Linux Containers with ease.
TL;DR:
It is possible to do a few more things more with docker besides working with containers, such as creating a root shell on the host, overwriting system configuration files, reading restricted stuff, etc.
more here..........http://reventlov.com/advisories/using-the-docker-command-to-root-the-host
TL;DR:
It is possible to do a few more things more with docker besides working with containers, such as creating a root shell on the host, overwriting system configuration files, reading restricted stuff, etc.
more here..........http://reventlov.com/advisories/using-the-docker-command-to-root-the-host
↧
A Starter Guide to Encryption and Fingerprinting
From time to time we are asked what the deal is with the 'Fingerprints' and the 'Keys' in our contact details. Now, I want to give you an explanation :) In order to do so, I am trying to give you a very brief overview about mail encryption, in which keys and fingerprints are generally used. But first of all, I want to point out, that this post does not address a technical audience. Instead, I want to write to non-technical persons like managers, project leaders, moms, dads and grand parents. As a consequence, I will ignore any mathematics and solely concentrate on the bare concept of mail encryption.
In the beginning, I will talk about goals and reasons of encryption. Afterwards I explain the basics of symmetric and asymmetric encryption. This leads to PGP and the usage of fingerprints. If questions arise, please do not hesitate to ask us (writing encrypted mail would be best).
more here.........https://splone.com/blog/2015/3/31/a-starter-guide-to-encryption-and-fingerprinting
In the beginning, I will talk about goals and reasons of encryption. Afterwards I explain the basics of symmetric and asymmetric encryption. This leads to PGP and the usage of fingerprints. If questions arise, please do not hesitate to ask us (writing encrypted mail would be best).
more here.........https://splone.com/blog/2015/3/31/a-starter-guide-to-encryption-and-fingerprinting
↧
How to own any windows network with group policy hijacking attacks
For those of you that didn’t make it to SyScan ‘15 last week, this is a blog post version of the presentation I gave about the vulnerabilities I found in group policy that resulted in Microsoft releasing MS15-011 and MS15-014 in February. These bulletins resolve issues in Microsoft’s group policy engine that allow remote code execution at SYSTEM level if an attacker can intercept network traffic from a domain-joined system.
The full process leading up to their discovery, along with exploitation details and accompanying video demonstrations, will be given. Additionally, the new security controls introduced by Microsoft will be discussed to assess how effective they are, show what attack scenarios they mitigate and which ones they do not. Finally, some additional guidance will be given on other mitigating controls that can provide additional protection will be discussed.
more here........https://labs.mwrinfosecurity.com/blog/2015/04/02/how-to-own-any-windows-network-with-group-policy-hijacking-attacks/
The full process leading up to their discovery, along with exploitation details and accompanying video demonstrations, will be given. Additionally, the new security controls introduced by Microsoft will be discussed to assess how effective they are, show what attack scenarios they mitigate and which ones they do not. Finally, some additional guidance will be given on other mitigating controls that can provide additional protection will be discussed.
more here........https://labs.mwrinfosecurity.com/blog/2015/04/02/how-to-own-any-windows-network-with-group-policy-hijacking-attacks/
↧
Website Malware – The SWF iFrame Injector Evolves
ast year, we released a post about a malware injector found in an Adobe Flash (.SWF) file. In that post, we showed how a .SWF file is used to inject an invisible, malicious iFrame.
It appears that the author of that Flash malware continued with this method of infection. Now we are seeing more varieties infecting both WordPress and Joomla websites. Though it’s uncertain how many iterations existed in the wild when we first reported the issue, this time we’ve found a lot of websites where the infection looks similar
more here........http://blog.sucuri.net/2015/04/website-malware-the-swf-iframe-injector-evolves.html
It appears that the author of that Flash malware continued with this method of infection. Now we are seeing more varieties infecting both WordPress and Joomla websites. Though it’s uncertain how many iterations existed in the wild when we first reported the issue, this time we’ve found a lot of websites where the infection looks similar
more here........http://blog.sucuri.net/2015/04/website-malware-the-swf-iframe-injector-evolves.html
↧
↧
Push it, Push it Real Good
My boss comes from a red teaming background; I do not. When I started to move beyond simple pentests and absorb his more advanced tradecraft, I was amazed that I hadn’t heard of much of it before. I wondered why there wasn’t more public information on these powerful tactics, techniques, and procedures. Now that I have a bit better of a grasp on red teaming, I think I might know why.
more here.........http://www.harmj0y.net/blog/redteaming/push-it-push-it-real-good/
more here.........http://www.harmj0y.net/blog/redteaming/push-it-push-it-real-good/
↧
NEW : VMSA-2015-0003 VMware product updates address critical information disclosure issue in JRE
Advisory ID: VMSA-2015-0003
Synopsis: VMware product updates address critical information disclosure issue in JRE.
Issue date: 2015-04-02
Updated on: 2015-04-02 (Initial Advisory)
CVE number: CVE-2014-6593, for other CVEs see JRE reference
Synopsis: VMware product updates address critical information disclosure issue in JRE.
Issue date: 2015-04-02
Updated on: 2015-04-02 (Initial Advisory)
CVE number: CVE-2014-6593, for other CVEs see JRE reference
↧
WhatsApp Open Security Write Up
This bizarre story is true of the BugBоunty program from WhаtsApp, the property of Facebook but as of December 11, 2014 I had not received a reply.
more here.......http://w0rmin.blogspot.com/2015/04/whatsapp-open-security-write-up.html
PS: Blog is in Russian so unless you speak the language you will need translation software or a human translator
more here.......http://w0rmin.blogspot.com/2015/04/whatsapp-open-security-write-up.html
PS: Blog is in Russian so unless you speak the language you will need translation software or a human translator
↧
The story of a pentester recruitment
Last year we decided to expand our pentest team, and we figured that offering a hands-on challenge would be a good filter for possible candidates, since we’ve accumulated quite a bit of experience from organizing wargames and CTF at various events. We provided an isolated network with three hosts and anyone could apply by submitting a name, and email address and a CV – we’ve sent VPN configuration packs to literally everyone who did so.
more here........http://blog.silentsignal.eu/2015/04/03/the-story-of-a-pentester-recruitment/
more here........http://blog.silentsignal.eu/2015/04/03/the-story-of-a-pentester-recruitment/
↧
↧
x64_dbg debugger for windows 2.4 alpha release
The changelog states there is now Yara pattern finding support and more here....http://x64dbg.com/changelog.html
![interface]()
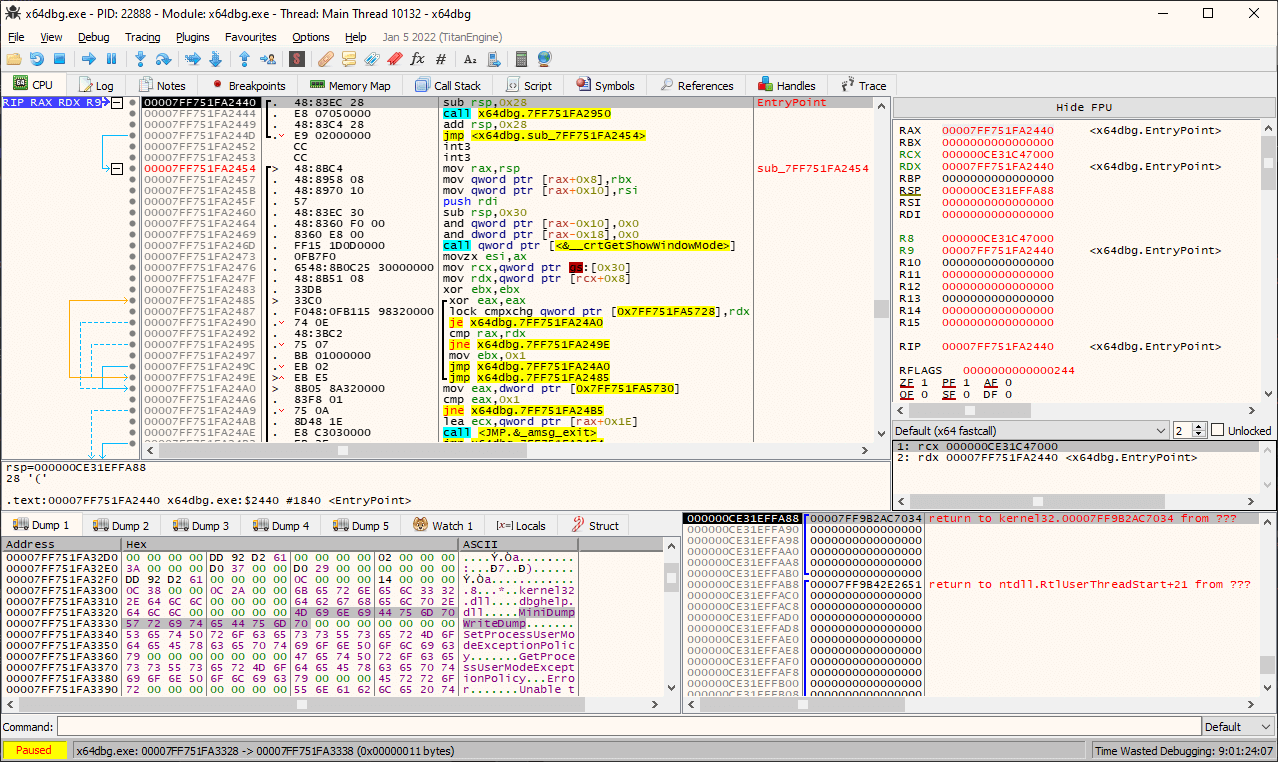
↧
Google Report: Android Security 2014 Year in Review
We’re committed to making Android a safe ecosystem for users and developers. That’s why we built Android the way we did—with multiple layers of security in the platform itself and in the services Google provides. In addition to traditional protections like encryption and application sandboxes, these layers use both automated and manual review systems to keep the ecosystem safe from malware, phishing scams, fraud, and spam every day.
Android offers an application-focused platform security model rooted in a strong application sandbox. We also use data to improve security in near real time through a combination of reliable products and trusted services, like Google Play, and Verify Apps. And, because we are an open platform, third-party research and reports help make us stronger and users safer.
But, every now and then we like to check in to see how we’re doing. So, we’ve been working hard on a report that analyzes billions (!) of data points gathered every day during 2014 and provides comprehensive and in-depth insight into security of the Android ecosystem.
report here......https://static.googleusercontent.com/media/source.android.com/en/us/devices/tech/security/reports/Google_Android_Security_2014_Report_Final.pdf
Android offers an application-focused platform security model rooted in a strong application sandbox. We also use data to improve security in near real time through a combination of reliable products and trusted services, like Google Play, and Verify Apps. And, because we are an open platform, third-party research and reports help make us stronger and users safer.
But, every now and then we like to check in to see how we’re doing. So, we’ve been working hard on a report that analyzes billions (!) of data points gathered every day during 2014 and provides comprehensive and in-depth insight into security of the Android ecosystem.
report here......https://static.googleusercontent.com/media/source.android.com/en/us/devices/tech/security/reports/Google_Android_Security_2014_Report_Final.pdf
↧
Elements of Programming Interviews
The programming exercises in EPI are representative of what you will be asked in an interview here....http://elementsofprogramminginterviews.com/
↧
FreeSentry Mitigating use-after-free Vulnerabilities
Talos is constantly researching the ways in which threat actors take advantage of security weaknesses to exploit systems. Use-after-free vulnerabilities have become an important class of security problems due to the existence of mitigations that protect against other types of vulnerabilities, such as buffer overflows. Today, Talos is releasing FreeSentry, a mitigation for use-after-free vulnerabilities.
additional info here......http://blogs.cisco.com/security/talos/freesentry
additional info here......http://blogs.cisco.com/security/talos/freesentry
↧
↧
AllCrypt.com is still down
Here is https://www.allcrypt.com/sitedown.html
and the last updated blog post link here.....https://www.allcrypt.com/blog/2015/03/what-happened-and-whats-going-on/
↧
IBM RESEARCH AND INTELLIGENCE REPORT : THE DYRE WOLF: ATTACKS ON CORPORATE BANKING ACCOUNTS
What do the "Dire Wolf", "Wolf in Sheep's Clothing", and the "Wolf of Wall Street" have in common? Deception, and a ferocious appetite to get what they want. Now, enter “The Dyre Wolf”. This is a new campaign that utilizes the now popular Dyre, or Dyreza, malware directly targeting corporate banking accounts and has successfully stolen upwards of a million dollars from unsuspecting companies. The “Dyre Wolf”, in this case, wants money.
IBM Managed Security Services (MSS) working with Emergency Response Services (ERS) have been tracking a new campaign with a formidable success rate. The organization behind the Dyre malware campaign has not only consistently updated and maintained the malware, they have added more tricks to further their deception. Social engineering via phone calls and denial of service are now part of their toolkit. IBM MSS is tracking several Dyre Wolf incidents across multiple industries and verticals.
read more here..........https://portal.sec.ibm.com/mss/html/en_US/support_resources/pdf/Dyre_Wolf_MSS_Threat_Report.pdf
IBM Managed Security Services (MSS) working with Emergency Response Services (ERS) have been tracking a new campaign with a formidable success rate. The organization behind the Dyre malware campaign has not only consistently updated and maintained the malware, they have added more tricks to further their deception. Social engineering via phone calls and denial of service are now part of their toolkit. IBM MSS is tracking several Dyre Wolf incidents across multiple industries and verticals.
read more here..........https://portal.sec.ibm.com/mss/html/en_US/support_resources/pdf/Dyre_Wolf_MSS_Threat_Report.pdf
↧
CuckooDroid-Automated Malware Android Analysis
CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files, CuckooDroid brigs to cuckoo the capabilities of execution and analysis of android application.
more here........https://github.com/idanr1986/cuckoo-droid
more here........https://github.com/idanr1986/cuckoo-droid
↧
