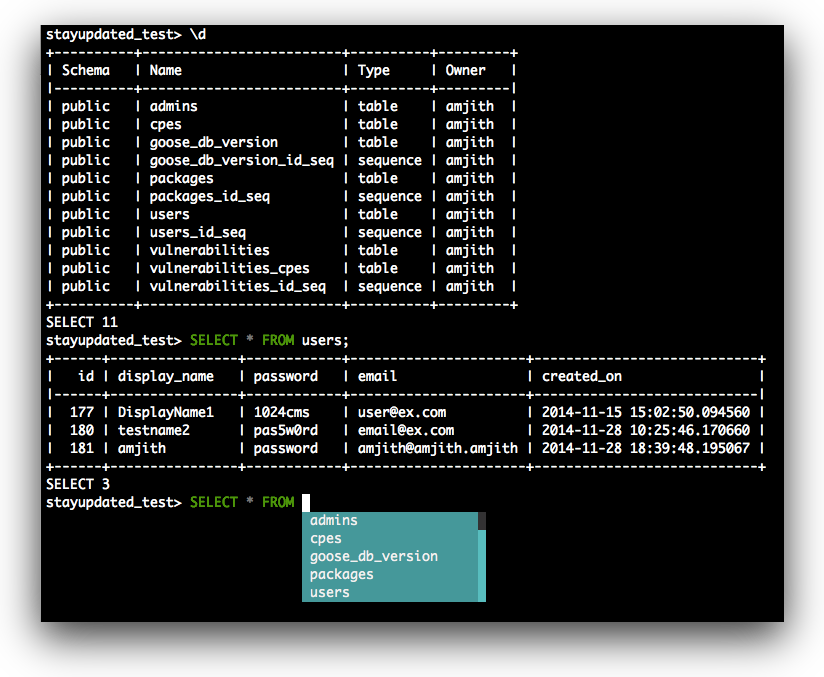
Pgcli is a command line interface for Postgres with auto-completion and syntax highlighting
more here......http://pgcli.com/index
![Screenshot]()
more here......http://pgcli.com/index
#Affected Vendor: http://pligg.com/
#Date: 23/04/2015
#Discovered by: Joel Vadodil Varghese
#Type of vulnerability: Persistent XSS
#Tested on: Windows 8.1
#Product: Pligg CMS
#Version: 2.0.2
#Tested Link: http://localhost/pligg/admin/admin_page.php
Description: Pligg CMS is a content management platform that powers tens of thousands of websites. It specializes in
creating social publishing networks, where users submit and promote content similar to sites like Digg, Reddit, and
Mixx.Pligg CMS is vulnerable to stored xss vulnerability. The parameter "page_title" and "page_content" are the
vulnerable parameter which will lead to its compromise.
#Proof of Concept (PoC): "><img src="a.jpg" onerror="alert('XSS')"/>
#Title : Avsarsoft Matbaa Script - Multiple Vulnerabilities
#Author : ZoRLu / zorlu () milw00rm com
#Website : milw00rm.com / milw00rm.net / milw00rm.org
#Twitter : https://twitter.com/milw00rm or @milw00rm
#Test : Windows7 Ultimate
#Discovery : 15/04/15
#Publish : 23/04/15
#Thks : exploit-db.com, packetstormsecurity.com, securityfocus.com, sebug.net, cxsecurity.com and others
#BkiAdam : Dr.Ly0n, KnocKout, LifeSteaLeR, Nicx
#Demo : http://avsarsoft.com/matbaa/
#Demo User : sop08574 () qisdo com
#Demo Pass : 123456
1) Remote File Upload Vulnerability
you go here:
localhost/path/index.php?Git=KartvizitTasarla
localhost/path//index.php?Git=BrosurTasarla
localhost/path/index.php?Git=DavetiyeTasarla
after click to "Resim Ekle"
select your php file and wait for upload
after go here for you php file
localhost/path/upload/file.php
1) Multiple XSS Vulnerabilities
register to site
localhost/path/index.php?Git=UyeOl
after login
localhost/path/index.php?Git=Uyelik
after go here and add your xss code
localhost/path/index.php?Git=KontrolPaneli&Sayfa=KisiselBilgilerim
localhost/path/index.php?Git=KontrolPaneli&Sayfa=AdresBilgilerim
localhost/path/index.php?Git=KontrolPaneli&Sayfa=Yorumlar
Author: Nicholas Lemonias
Advisory Date: 23/4/2015
4k Satellite Security Research - DVB-S2X Standard Evaluation Notes
# . . . . . . .
# . . . . . ______
# . . . ////////
# . . ________ . . ///////// . .
# . |.____. /\ .///////// .
# . .// \/ |\ /////////
# . . .// \ | \ ///////// . . .
# ||. . .| | ///////// . .
# . . || | |//`,///// .
# . \\ ./ // / \/ .
# . \\.___./ //\` ' ,_\ . .
# . . \ //////\ , / \ . .
# . ///////// \| ' | .
# . . ///////// . \ _ / .
# ///////// .
# . .///////// . .
# . -------- . .. .
# . . . . .
# ________________________
# ____________------------ -------------_________
-=[ Advanced Information Security Corporation ]=-
Abstract
==========
During a security evaluation of the Digital Video Broadcasting for
Satellite-S2X (Extended) for UHD/4K compatible ecosystems; conducted
internally by the Advanced Information Security
Group, instances of insecure function use were observed, which could
lead to exploitation of these systems.
Introduction
==========
Ultra High Definition is rapidly growing into the next revolution of
virtual reality,
beyond HDTV. Ultra HD envisages to deliver a surreal cinematic
experience, to the next generation broadcasting world. Ultra High
Definition is a digital format that can process and deliver 4k and 8k
pixel resolution data.
The prolonged encoding rates operate on the basis of an equilibrated
analogy of up to 60 fps. Thus the higher the frame rates , the higher
are also the demands in data transfer technology.
High Bandwidth content utilize hybrid architectures and make use of
fiber optic technologies, cable networks, wireless architectures and
high powered DTH satellite broadcasting systems. DTH satellites
operate at higher frequency rates mostly at the Ka band or higher.
The Japanese Government was one of the first to practically implement
the UHD 4K System over satellite, in practice. In their experiment
prominent environmental predicaments concluded to modifications of
modulation methods due to rain attenuation issues. It is pertinent to
note, that however no security considerations were mentioned in their
experiment.
During an internal security evaluation of the extended version of
(DVB-S2X), multiple security predicaments were observed.
Review of DVB-S2X
================
The DVB-S2X is the extended version of DVB-S2 which was officially
presented by the DVB Consortium in 2014.
The new standard provides a number of technical enhancements for
support of DVB-S2X ecosystems; such as an improvised and faster
modulation for the delivery of UHD Services, however during our
security evaluation no security considerations are made.
Therefore it is pertinent to note that the older versions of DVB/S2
and current DVB/S2X (Extended) do support a fully-fledged Internet
Protocol interoperation.
The DVB-S2X offers very-low carrier-to-noise and low-carrier to
interference ratios, below 10 –db. (SNR) which makes it suitable for
professional and even military deployments.
Although, the following enhancements are made:
• Low roll off and smaller carrier spacing.
• Advanced Filtering technologies for bandwidth.
• Forward Error Correction Enhancements with added support for (64,
128, 256APSK) for professional and military applications, for extended
requirements, improved spectral efficiency and increased granularity.
• Bonding mechanisms for streams of TV data.
• Improvements for Optimal Modulation (MODCOD).
• A very low SNR MODCOD to support mobile architectures from land, sea
and air. Additional modulation enhancements have been provided in the
QPSK and BPSK range, in order to enhance atmospheric interference
protection mechanisms.
• The VLSNR MODCOD packet header was modified with the inclusion of a
PLH (Physical Layer header) and the addition of a significantly better
error correction coding system.
• Wideband Support for improved signal propagation.
During our evaluation it was asserted that the current composition of
DVB/S2x fails significantly to adhere to best practice and security
fundamentals. There are no security controls entailed for the
provision of fundamental security services of Confidentiality,
Integrity, Availability, (Non-Repudiation and Data Origin
Authentication). Although a two-way scrambling method is entailed,
that cannot substitute encryption.
This security issue stems from the lack of encryption of plain-text
information, as it is received by an L2 source, throughout the
encapsulation of information. Current implementations use Standard
Internet Security Protocols to bridge the gap.
The lightweight architecture of protocols such MPEG-2/MPEG-4, can be
subtle to overhead and service degradation;
This affects DVB-S2 and S2x compatible ecosystems that transmit
information using MPEG-2 over IP / MPEG-4 TS protocol over IP, which
make them subtle to eavesdropping attacks.
The DVB/S2 and DVB/S2X supports a fully-fledged IP interoperation.
Therefore this current composition of DVB/S2X fails to address the
inherent security instances at the core of the problem, during its
embryonic stages.
Security consideration should be made using a rather pedantic layered
approach to security.
Current designs of HEVC modulation (in DVB/S2X) lack fundamental
security services such as those of Confidentiality, Integrity,
Availability and Non-Repudiation.
It is pertinent to note that the DVB/S2x support for backward
compatibility, with MPEG-2 over IP which can be abused by
threat-actors.
Technological and market transformation from DVB/S2 to DVB-S2x is a
lengthy process for manufacturers and satellite service providers
alike.
4The importance of confidentiality is paramount for the protection and
prevention of unauthorized access to private information.
A malicious attacker could take advantage of this lack of security
services, to passively wiretap bits of plain-text information. HEVC
Fuzzing techniques can be used for the extraction of information that
may be contained in HEVC bit-stream structures and access units.
Attacks against 4K ecosystems
============================
Man-in the middle attacks
Repudiation Attacks
Denial of Service attacks against the actual satellite ecosystem
(while in orbit)
Replaying & Reordering attacks
MPEG-2 and H.264/MPEG-4 vulnerabilities
===================================
Thus in a MPEG-2 – TS transmission, the network identifies the “TS
logical channel”, and the PDU units received.
For instance a Transport Stream contains multiplexed data , multiple
packet sources, entailing the payload from a number of PES data
streams.
This lack of integrity and data origin authentication in the
encapsulated MPEG-2 Transport Stream packets over DVB-S2X can be
problematic.
Attacks that seek to fabricate, falsify, alter or delete information
are feasible due to the lightweight protocol characteristics.
Whilst current methodologies suggest that encryption can be provided
using standard Internet Security Protocols such as IPSEC, this only
bridges the gaps.
Another security problem arising from the lack of confidentiality and
integrity, is that the plain-text streams contain hardware MAC or NPA
addresses of the participating L2 destination.
Conclusion
============
However the Internet Protocol Security (IPSEC) provides advantageous
considerations in MPEG-2 over IP in satellite infrastructures, and
such are: interoperability; it does also present a trade-off between
Quality of Service.
Satellite security over 4k broadcasting is reliant on standard
security protocols to address inherent security issues.
Citing an example, an IPsec security gateway in tunnel mode, would
reveal disadvantages in terms of network overhead and QoS.
ML-IPSEC
==========
ML-IPsec attempts to address the problems arising from the use of
IPsec, although the issue of mobility is presented, which creates a
plethora of other issues to service providers and users alike.
SSL Vulnerabilities
================
Ecosystems that make use of SSL , are prone to a variety of attacks.
In the light of recent issues; FREAK SSL/TLS, BEAST, Heart Bleed, DoS
attacks (NULL pointer dereference / memory exhaustion) are some of the
vulnerabilities affecting SSL implementations.
References
============
US CERT, (2015). FREAK-SSL Vulnerability. [online] Available at:
https://www.us-cert.gov/ncas/current.../FREAK-SSLTLS-Vulnerability
[Accessed 23 Apr. 2015].
DVB Consortium, (2015). DVB-S2X. [online] Available at:
http://www.dvb.org/resources/public/standards/a83-2_dvb-s2x_den302307-2.pdf
[Accessed 23 Apr. 2015].
Securityfocus Website, (2015). OpenSSL Advisory.. [online] Available
at: http://www.securityfocus.com/archive/1/535167 [Accessed 23 Apr.
2015].
Us-cert.gov, (2015). OpenSSL 'Heartbleed' vulnerability
(CVE-2014-0160) | US-CERT. [online] Available at:
https://www.us-cert.gov/ncas/alerts/TA14-098A [Accessed 23 Apr. 2015].